AV-Comparatives is pleased to announce the renewal of its ISO 9001:2015 certification for the independent testing of anti-virus software. TÜV Austria has reaffirmed AV-Comparatives’ commitment to provide “Independent Tests of Anti-Virus Software” by extending the certification, validating the organization’s dedication to delivering high-quality evaluations in the field of IT security.
Tag: certification
AV-Comparatives’ Award Ceremony for 2023
AV-Comparatives’ Security Summit and Award Ceremony 2024 recognised paramount cybersecurity solutions for enterprises and consumers.
Consumer Summary Report 2023
Austrian antivirus testing lab AV-Comparatives has released its annual Summary Report for consumer security products (PDF available here). This includes results of all the individual Windows tests carried out during 2023, a user-interface review for all 16 tested products, and awards given to individual programs in various categories.
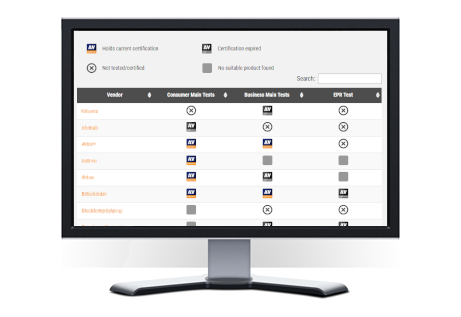
IT Security Products Overview
In response to the ever-evolving digital landscape, we’re excited to introduce the “IT Security Products Overview.” This compilation features 50 respected vendors, offering a practical guide for those looking to make informed decisions in the realm of cybersecurity. https://www.av-comparatives.org/security-products-overview/
Upcoming AV-Comparatives’ Certification Tests 2024
As in previous years, we will be running certification tests for the following products:
- Anti-malware programs for macOS
- Anti-malware apps for Android
- Phishing protection for Windows and other platforms
- Parental control features for Windows and other platforms
- VPN programs for Android and Windows
We also offer comprehensive security assessments exclusively for enterprise products, covering enterprise security tests, EPR/XDR tests, and penetration/red-teaming evaluations.
Security vendors interested in participating in any of the aforementioned tests or seeking more details are invited to contact us by 31st of March 2024.
Business Security Test August-November 2023
The second half-year report of AV-Comparatives’ 2023 Enterprise Main-Test Series, covering Real-World Protection, Malware Protection and Performance Tests, has been released. Product reviews are also included in the report, which can be found here: https://www.av-comparatives.org/tests/business-security-test-2023-august-november
NGFW Egress C2 Test: Assessing the Effectiveness of Outgoing Network Traffic Prevention and Detection Capabilities
In June 2023, AV-Comparatives conducted an NGFW Egress C2 Test to evaluate the effectiveness of NGFW products in detecting and preventing malicious traffic. In targeted attacks, one of the goals of APT groups is to establish control over a compromised system by opening a command-and-control channel (C2) to the command-and-control server operated by the attacker. If the attacker has already gained access to the system via a trusted relationship, or has delivered malware using phishing or USB drives, they can use C2 malware to open the C2 channel.
Business Security Test March-June 2023
The first half-year report of AV-Comparatives’ 2023 Enterprise main-test series containing a Real-World Protection, Malware Protection and Performance Test has been released. Product reviews are also included in the report, which can be found here: https://www.av-comparatives.org/tests/business-security-test-2023-march-june
Mobile Security Review 2023
AV-Comparatives’ latest Mobile Security Report 2023 is now available. Nine security products for Android have been thoroughly tested and reviewed. https://www.av-comparatives.org/tests/mobile-security-review-2023/
Mac Security Review/Test 2023
We have reviewed and tested nine security solutions on Apple’s macOS Ventura. Read our Mac Security Test & Review 2023 to see which security solutions have been approved.