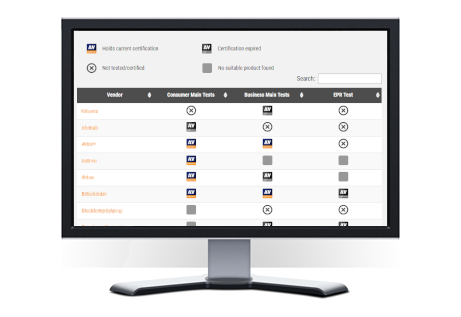
In response to the ever-evolving digital landscape, we’re excited to introduce the “IT Security Products Overview.” This compilation features 50 respected vendors, offering a practical guide for those looking to make informed decisions in the realm of cybersecurity. https://www.av-comparatives.org/security-products-overview/
Tag: enterprise
Business Security Test August-November 2023
The second half-year report of AV-Comparatives’ 2023 Enterprise Main-Test Series, covering Real-World Protection, Malware Protection and Performance Tests, has been released. Product reviews are also included in the report, which can be found here: https://www.av-comparatives.org/tests/business-security-test-2023-august-november
Advanced Threat Protection (ATP) Test 2023
AV-Comparatives has released the results of its 2023 Advanced Threat Protection Tests. Seven consumer antivirus products and eight enterprise endpoint-security programs for Windows were put through their paces.
https://www.av-comparatives.org/testmethod/advanced-threat-protection-tests/
Endpoint Prevention & Response (EPR) Test 2023
AV-Comparatives has released its Endpoint Prevention and Response (EPR) Test, taking into account the total cost of ownership (TCO) of each product, potential breach costs, and operational/accuracy costs.
https://www.av-comparatives.org/tests/endpoint-prevention-response-epr-test-2023/
Business Test Factsheet August-September 2023
We released the August-September factsheet of the Business Main-Test Series. You can find the factsheet here:
https://www.av-comparatives.org/tests/business-security-test-august-september-2023-factsheet/
The full and more detailed report – containing also a Performance test and product reviews – will be released in December.
The difference between AV-Comparatives’ EPR Test and MITRE ATT&CK Engenuity
Both the AV-Comparatives EPR Test and MITRE Engenuity have their merits, each providing useful insights into endpoint security solutions. Understanding the differences between these two tests is essential for IT managers, CISOs, and other tech-savvy professionals looking to select endpoint security solutions that will effectively protect their environments.
NGFW Egress C2 Test: Assessing the Effectiveness of Outgoing Network Traffic Prevention and Detection Capabilities
In June 2023, AV-Comparatives conducted an NGFW Egress C2 Test to evaluate the effectiveness of NGFW products in detecting and preventing malicious traffic. In targeted attacks, one of the goals of APT groups is to establish control over a compromised system by opening a command-and-control channel (C2) to the command-and-control server operated by the attacker. If the attacker has already gained access to the system via a trusted relationship, or has delivered malware using phishing or USB drives, they can use C2 malware to open the C2 channel.
Business Security Test March-June 2023
The first half-year report of AV-Comparatives’ 2023 Enterprise main-test series containing a Real-World Protection, Malware Protection and Performance Test has been released. Product reviews are also included in the report, which can be found here: https://www.av-comparatives.org/tests/business-security-test-2023-march-june
Anti-Tampering Certification Test
AV-Comparatives has published the results of the Anti-Tampering Certification Test on its website, complete with detailed information about the methodology and criteria used in the evaluation. Each year, AV-Comparatives offers a focus test, allowing vendors to apply for certification. This year, the emphasis was on “Defense Evasion” (Anti-Tampering). Both vendors and customers are encouraged to review the results and use them to make informed decisions regarding cybersecurity solutions.
https://www.av-comparatives.org/news/anti-tampering-certification-test/
Business Security Test August-November 2022
The second half-year report of AV-Comparatives’ 2022 Enterprise Main-Test Series, covering Real-World Protection, Malware Protection and Performance Tests, has been released. Product reviews are also included in the report, which can be found here: https://www.av-comparatives.org/tests/business-security-test-2022-august-november